Incident Overview
On July 19, 2024, at 04:09 UTC, CrowdStrike deployed a sensor configuration update to Windows systems. This update, part of the Falcon platform's routine protection measures, led to an unexpected logic error, causing system crashes and blue screen errors (BSOD) on affected systems.
The issue was promptly resolved, and the problematic configuration update was corrected by 05:27 UTC the same day. It is important to note that this issue was not caused by a cyberattack.
Impact Assessment
Users running Falcon sensor for Windows version 7.11 and above, who were online between 04:09 UTC and 05:27 UTC on July 19, 2024, could have been impacted. Systems that received the update during this window were particularly at risk of crashing.
Configuration File Details
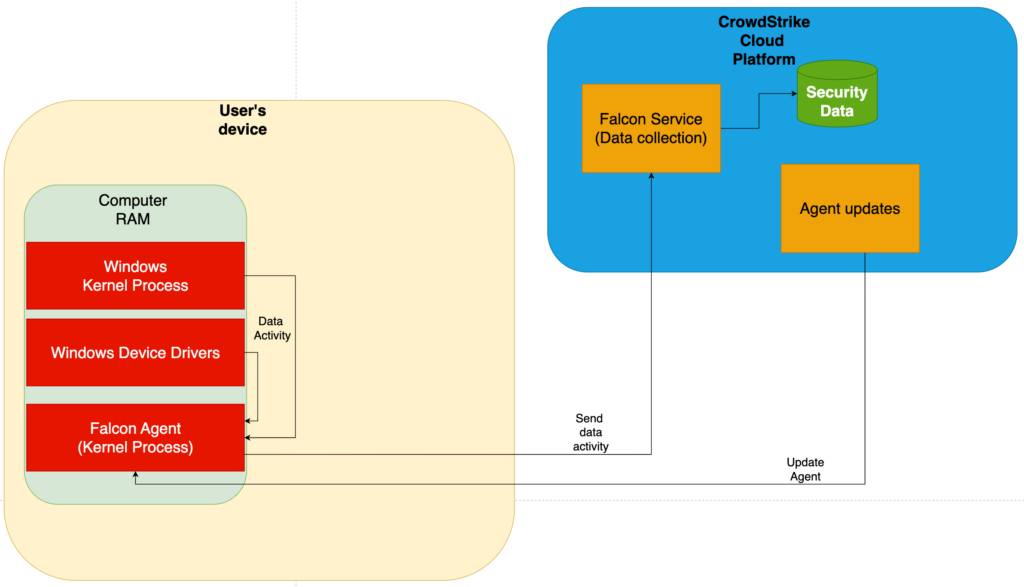
The configuration files, known as "Channel Files," are a part of the Falcon sensor's behavioral protection framework. These files are regularly updated to counter new tactics and techniques identified by CrowdStrike. This update process, in place since Falcon's inception, typically occurs multiple times daily.
Technical Explanation
On Windows systems, Channel Files are stored in:
C:\Windows\System32\drivers\CrowdStrike\
These files are named with a "C-" prefix and a unique identifier number. The Channel File involved in this incident is 291, with filenames starting "C-00000291-" and ending with a .sys extension. Despite the .sys extension, these files are not kernel drivers.
Channel File 291 is responsible for how Falcon assesses named pipe executions on Windows systems. Named pipes facilitate interprocess or intersystem communication in Windows. The update, intended to target malicious named pipes used in cyberattacks, caused an OS crash due to a logic error.
Resolution Steps
CrowdStrike has rectified the logic error in Channel File 291. No further changes to this file are required, and Falcon continues to protect against the misuse of named pipes. This issue was not related to null bytes in Channel File 291 or any other file.
Remediation Information
For the most current remediation advice and information, customers are encouraged to visit the CrowdStrike blog or Support Portal. Customers with specific support needs should contact CrowdStrike directly. Systems that were not affected will continue to function normally and are not at risk of experiencing this issue. Systems running Linux or macOS do not use Channel File 291 and were not affected.
Root Cause Analysis
CrowdStrike is conducting a detailed root cause analysis to understand how this logic flaw occurred. This investigation aims to identify improvements in foundational processes and workflows. Updates on the findings will be provided as the analysis continues.
Lessons Learned
- Rapid Response: Quickly identifying and fixing the issue helped minimize its impact.
- Effective Communication: Providing clear and timely updates to customers is crucial during incidents.
- Process Enhancements: The incident underscores the importance of rigorous testing and validation for updates.
- Continuous Improvement: Ongoing evaluation of update mechanisms to prevent future issues.
By addressing these areas, CrowdStrike aims to strengthen the reliability and effectiveness of its protection mechanisms.
References:

